Envescent can put together the pieces of your business' IT puzzle
Envescent can put together the pieces of your business' IT puzzle We can help your company recover from a breach
We can help your company recover from a breach We'll help you find the right cybersecurity solutions
We'll help you find the right cybersecurity solutions Protect your company from the growing threat of cyber attacks
Protect your company from the growing threat of cyber attacks Envescent specializes in comprehensive cybersecurity audits
Envescent specializes in comprehensive cybersecurity audits Mitigate risk with professional penetration testing services
Mitigate risk with professional penetration testing services
Harness the Power of AI
Our AI experts can help your business realize the benefits of machine learning, large scale data analytics, automation and much more.Cybersecurity Training Classes
81% of data breaches are the result of human-related security failures, we address this by providing training on the latest threats and how best to mitigate themCybersecurity Assessments
Envescent specializes in cybersecurity assessments, providing comprehensive audits that focus on comprehensively identifying security vulnerabilitiesProfessional IT Consulting
Fast, friendly and professional information technology consulting services from our team of seasoned experts
Upgrade to Microsoft 365
Cloud collaboration can improve your company's productivity, and can help provide turnkey Microsoft 365 solutions to get therePenetration Testing
Simulate how a malicious hacker may compromise your critical business networks and systems with our cutting edge penetration testing services
The Value of DNS Blacklisting
In today’s increasingly interconnected world, cyber threats are becoming more sophisticated and widespread. As a result, it is more important than ever for individuals and organizations to take proactive measures to protect themselves from potential harm.
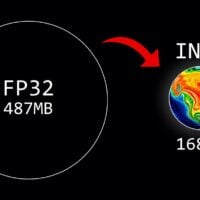
What Does Quantization Mean and How Does It Shrink AI Models?
Quantization is a technique used to reduce the size of machine learning models while maintaining accuracy. This can lead to faster deployment times, lower memory usage, and reduced bandwidth requirements when deploying these models on edge devices or in other resource-constrained environments.
Social Engineering Attacks: Evolving Threats and Proactive Measures
Social engineering attacks have been a persistent threat in the cybersecurity landscape, preying on human vulnerabilities rather than technical weaknesses. As technology continues to advance, so too do these tactics, becoming more sophisticated and convincing.
The Latest Trends in Artificial Intelligence
Artificial Intelligence (AI) is a rapidly evolving field that has seen significant advancements in recent years. As AI technology continues to develop and mature, new trends are emerging that are shaping the future of this exciting industry. In this article, we will discuss some of the latest trends in AI that are currently capturing the attention of researchers, developers, and users alike.
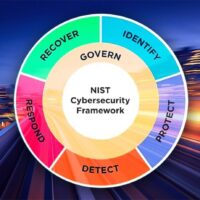
The Updated NIST Cybersecurity Framework 2.0
The National Institute of Standards and Technology (NIST) has recently updated its Cybersecurity Framework for 2024. This is an important development that businesses need to take into account when developing their own cybersecurity best practices. In this article, we will discuss the changes made by NIST and how businesses can use these updates as a reference point for their own cybersecurity frameworks.